Wiretapping occurs all the time in espionage and crime movies. Spies and gangsters know the enemy is listening, so they speak in code over the phone and keep an eye out for bugs. In the real world, we may not think much about wiretapping. Most of the time, we assume our phone lines are secure. And in most cases, they are, but only because nobody cares enough to listen in. If people did want to eavesdrop, they could tap into almost any phone line quite easily.
In this article, we'll explore the practice of wiretapping to see just how simple it is. We'll also look at a few different types of wiretaps, find out who taps phone lines and examine the laws that regulate this practice.
Advertisement
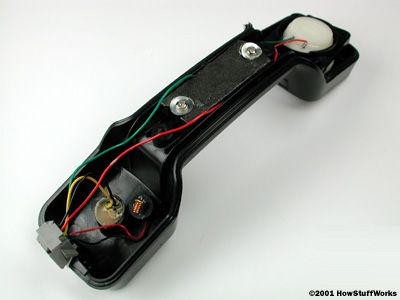
To learn how wiretapping works, you first have to understand the basics of telephones. If you take a look inside a telephone cord, you'll see how simple phone technology is. When you cut off the outer covering, you'll find two copper wires, one with a green covering and one with a red covering. These two wires make up much of the path between any two phones.

The copper wires transmit the fluctuating sound waves of your voice as a fluctuating electrical current. The phone company sends this current through the wires, which are connected to the phone's speaker and microphone. When you speak into the receiver, the sound produces air-pressure fluctuations that move the microphone diaphragm back and forth. The microphone is hooked up so that it increases or decreases resistance (on the current running through the wire) in sync with the fluctuation in air pressure felt by the microphone diaphragm.
The varying current travels to the receiver in the phone on the other end and moves that phone's speaker driver. The heart of the driver is an electromagnet, which is attached to a diaphragm and suspended in front of a natural magnet. The wire carrying the varying electrical current winds around the electromagnet, giving it a magnetic field that repels it from the natural magnet. When the current voltage increases, the electromagnet's magnetism increases, and it pushes farther away from the natural magnet. When the voltage decreases, it slips back. In this way, the varying electrical current moves the speaker diaphragm back and forth, recreating the sound picked up by the microphone on the other end.
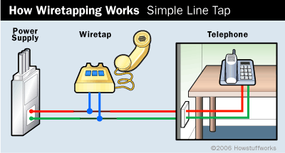
In its path through the global phone network, the electrical current is translated into digital information so that it can be sent quickly and efficiently over long distances. But ignoring this step in the process, you can think of the phone connection between you and a friend as one very long circuit that consists of a pair of copper wires and forms a loop. As with any circuit, you can hook up more loads (components powered by the circuit) anywhere along the line. This is what you're doing when you plug an extra phone into a jack in your house.
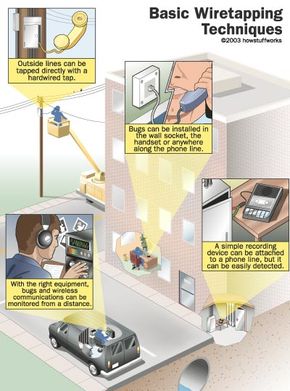
This is a very convenient system, because it's so easy to install and maintain. Unfortunately, it's also very easy to abuse. The circuit carrying your conversation runs out of your home, through your neighborhood and through several switching stations between you and the phone on the other end. At any point along this path, somebody can add a new load to the circuit board, in the same way you can plug a new appliance into an extension cord. In wiretapping, the load is a device that translates the electrical circuit back into the sound of your conversation.
This is all wiretapping is -- connecting a listening device to the circuit carrying information between phones. In the next few sections, we'll look at a few specific wiretaps and find out where they're connected to the circuit.
Advertisement